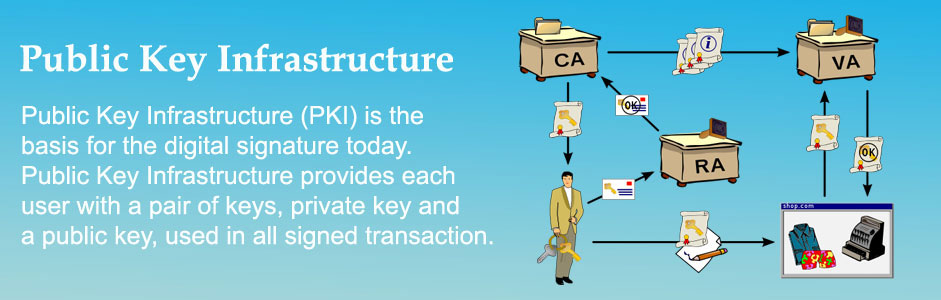
Public Key Infrastructure (PKI) is the basis for the digital signature today. Public Key Infrastructure provides each user with a pair of keys, private key and a public key, used in all signed transaction. The private key, as the name implies, is not shared and is used only by the signer to electronically sign documents. The public key is openly available and used by those that required to validate the signer’s digital signature. Public Key Infrastructure encompasses different components which include a Certificate Authority (CA), end-user enrollment software, and tools for managing, renewing and revoking keys and certificates.
A PKI is a system for the creation, storage, and distribution of electronic certificates(Digital Signature) which are used to verify that a particular public key belongs to a certain entity. The ublic-key infrastructure creates electronic certificates which map public keys to entities, securely stores these certificates in a central repository and revokes them if needed.
A PKI consists of:
- A certificate authority (CA) that both issues and verifies the digital certificates
- A registration authority which verifies the identity of users requesting information from the CA
- A central directory—i.e., a secure location in which to store and index keys
- A certificate management system
- A certificate policy
Simple public-key infrastructure
Another alternative, which does not deal with public authentication of PKI, is the simple SPKI that grew out of three independent efforts to overcome the complexities of X.509 and PGP’s web of trust. Simple public-key infrastructure does not associate users with persons, since the key is what is trusted, rather than the person. Simple public-key infrastructure does not use any notion of trust, as the verifier is also the issuer. This is called an “authorization loop” in simple public-key infrastructure terminology, where authorization is integral to its design.
Usage examples
public-key infrastructures (PKIs) of one type or another, and from any of several vendors, including providing public keys and bindings to user identities which are utilized for:
- Encryption and sender authentication of e-mail messages (Example- using OpenPGP or S/MIME)
- Encryption and authentication of documents (Example- the XML Signature or XML Encryption standards if documents are encoded as XML)
- Authentication of users to applications (Example- client authentication with SSL and smart card logon, ). There’s experimental usage for digitally signed HTTP authentication in the Enigform and mod_openpgp projects
- Bootstrapping secure communication protocols, example SSL and Internet key exchange (IKE) . In both of these, initial set-up of a secure channel uses asymmetric key— Example- public-key—methods, whereas actual communication uses faster symmetric key—Example- secret key—methods.
- Mobile signatures are digital signatures that are created using a mobile device and rely on signature or certification services in a location independent telecommunication environment